industrial internet of things (IIoT)
What is the industrial internet of things?
The industrial internet of things (IIoT) is the use of smart sensors, actuators and other devices, such as radio frequency identification tags, to enhance manufacturing and industrial processes. These devices are networked together to provide data collection, exchange and analysis. Insights gained from this process aid in more efficiency and reliability. Also known as the industrial internet, IIoT is used in many industries, including manufacturing, energy management, utilities, oil and gas.
IIoT uses the power of smart machines and real-time analytics to take advantage of the data that dumb machines have produced in industrial settings for years. The driving philosophy behind IIoT is that smart machines aren't only better than humans at capturing and analyzing data in real time, but they're also better at communicating important information that can be used to drive business decisions faster and more accurately.
Connected sensors and actuators enable companies to pick up on inefficiencies and problems sooner, saving time and money while also supporting business intelligence efforts. In manufacturing specifically, IIoT has the potential to provide quality control, sustainable and green practices, supply chain traceability and overall supply chain efficiency. In an industrial setting, IIoT is key to processes such as predictive maintenance, enhanced field service, energy management and asset tracking.
How does IIoT work?
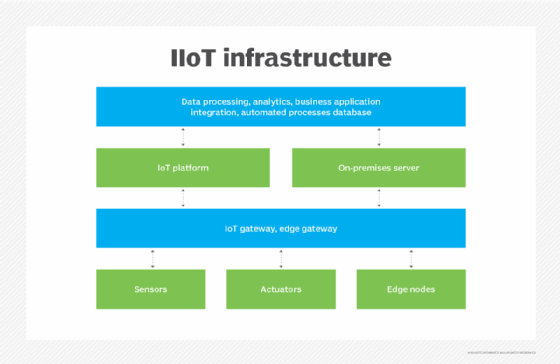
IIoT is a network of intelligent devices connected to form systems that monitor, collect, exchange and analyze data. Each industrial IoT ecosystem consists of the following:
This article is part of
Ultimate IoT implementation guide for businesses
- Connected devices that can sense, communicate and store information about themselves.
- Public and private data communications infrastructure.
- Analytics and applications that generate business information from raw data.
- Storage for the data that's generated by the IIoT devices.
- People.
These edge devices and intelligent assets transmit information directly to the data communications infrastructure, where it's converted into actionable information on how a certain piece of machinery is operating. This information can be used for predictive maintenance, as well as to optimize business processes.
What is the difference between IoT and IIoT?
Although the internet of things and IIoT have many technologies in common -- including cloud platforms, sensors, connectivity, machine-to-machine communications and data analytics -- they're used for different purposes.
IoT systems connect devices across multiple verticals, including agriculture, healthcare, enterprise, consumer, utilities, government and cities. IoT technology includes smart devices, fitness bands and other applications that generally don't create emergency situations if something goes amiss.
IIoT applications, on the other hand, connect machines and devices in sectors such as oil and gas, utilities and manufacturing. System failures and downtime in IIoT deployments can result in high-risk or life-threatening situations. IIoT applications are also more concerned with improving efficiency, health or safety versus the user-centric nature of IoT applications.
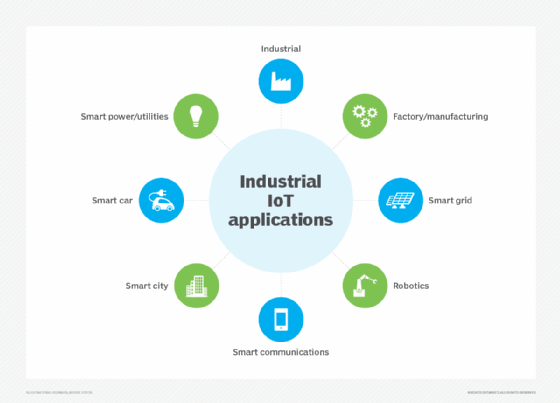
Which industries are using IIoT?
Numerous industries use IIoT, including the following:
- The automotive industry. This industry uses industrial robots, and IIoT can help proactively maintain these systems and spot potential problems before they can disrupt production. The automotive industry also uses IIoT devices to collect data from customer systems, sending it to the company's systems. That data is then used to identify potential maintenance issues.
- The agriculture industry. Industrial sensors collect data about soil nutrients, moisture and other variables, enabling farmers to produce an optimal crop.
- The oil and gas industry. Some oil companies maintain a fleet of autonomous aircraft that use visual and thermal imaging to detect potential problems in pipelines. This information is combined with data from other types of sensors to ensure safe operations.
- Utilities. IIoT is used in electric, water and gas metering, as well as for the remote monitoring of industrial utilities equipment such as transformers.
What are the benefits of IIoT?
IIoT devices used in the manufacturing industry offer the following benefits:
- Predictive maintenance. Organizations can use real-time data generated from IIoT systems to predict when a machine needs to be serviced. That way, the necessary maintenance can be performed before a failure occurs. This can be especially beneficial on a production line, where the failure of a machine might result in a work stoppage and huge costs. By proactively addressing maintenance issues, an organization can achieve better operational efficiency.
- More efficient field service. IIoT technologies help field service technicians identify potential issues in customer equipment before they become major issues, enabling techs to fix the problems before they affect customers. These technologies also provide field service technicians with information about which parts they need to make a repair. This ensures technicians have the necessary parts with them when making a service call.
- Asset tracking. Suppliers, manufacturers and customers can use asset management systems to track the location, status and condition of products throughout the supply chain. The system sends instant alerts to stakeholders if the goods are damaged or at risk of being damaged, giving them a chance to take immediate or preventive action to remedy the situation.
- Increased customer satisfaction. When products are connected to IoT, the manufacturer can capture and analyze data about how customers use their products, enabling manufacturers and product designers to build more customer-centric product roadmaps.
- Improved facility management. Manufacturing equipment is susceptible to wear and tear, which can be exacerbated by certain conditions in a factory. Sensors can monitor vibrations, temperature and other factors that could lead to suboptimal operating conditions.
Is IIoT secure?
Early on, manufacturers created IoT devices with little regard for security, resulting in the perception that IoT devices were inherently insecure. Given the similarities between IoT and IIoT devices, it's worth considering whether it's safe to use IIoT devices.
As with any other connected device, IIoT devices must be evaluated on a device-by-device basis. It's entirely possible that one manufacturer's device is secure while another's isn't. Even so, security is a bigger priority among device manufacturers than ever before. For example, security methods used in IIoT might include multifactor authentication, end-to-end encryption and the creation of custom authorization levels.
In 2014, several technology companies -- including AT&T, Cisco, General Electric, IBM and Intel -- formed the Industrial Internet Consortium (IIC), which was rebranded as the Industry IoT Consortium in 2020. Although this group's primary objective is to accelerate the adoption of IIoT and related technologies, it's made security a priority, even going so far as to form a security working group. The IIC's other working groups include technology, liaison, marketing, industry and digital transformation.
What are the risks and challenges of IIoT?
The biggest risks associated with IIoT use pertain to security. It's relatively common for IIoT devices to continue using default passwords, even after they've been put into production. Similarly, many IIoT devices transmit data as clear text. These conditions could make it relatively easy for an attacker to intercept the data coming from an IIoT device. Similarly, an attacker could take over an insecure IIoT device and use it as a platform for launching an attack against other network resources.
Security and device management are major challenges for those who are responsible for an organization's IIoT devices. As an organization adds more IIoT devices, it becomes increasingly important to adopt an effective device management strategy. More specifically, organizations must be able to positively identify IIoT devices to prevent the use of rogue devices. Establishing a means of identifying each individual device is also crucial for tasks such as replacing a failed device or performing a device refresh.
Patch management presents another challenge with IIoT devices. It's becoming more common for device manufacturers to issue periodic firmware updates. Organizations must have an efficient way to check devices to see if they have the latest firmware installed and deploy new firmware if necessary. In addition, such a tool must adhere to the organization's established maintenance schedule so it doesn't disrupt operations.
What are IIoT applications and examples?
In a real-world IIoT deployment of smart robotics, ABB, a power and robotics company, uses connected sensors to monitor the maintenance needs of its robots to prompt repairs before parts break.
Likewise, commercial jetliner maker Airbus launched what it calls the factory of the future, a digital manufacturing initiative to streamline operations and boost production. Airbus integrated sensors into machines and tools on the shop floor and outfitted employees with wearable tech -- e.g., industrial smart glasses -- aimed at reducing errors and enhancing workplace safety.
Another robotics manufacturer, Fanuc, has used sensors in its robotics, along with cloud-based data analytics, to predict the imminent failure of components in its robots. Doing so enables the plant manager to schedule maintenance at convenient times, reducing costs and averting potential downtime.
Magna Steyr, an Austrian automotive manufacturer, is using IIoT to track its assets, including tools and vehicle parts, as well as to automatically order more stock when necessary.
Who are IIoT vendors?
There are numerous vendors that offer IIoT platforms, including the following examples:
- ABB Ability. ABB specializes in connectivity, software and machine intelligence.
- Aveva. Acquired by Schneider Electric in early 2023, Aveva develops AI, digital transformation, IIoT and IoT edge platforms for original equipment manufacturers and end users.
- Cisco IoT. Cisco offers platforms for network connectivity, connectivity management, data control and exchange as well as edge computing.
- Fanuc. Fanuc combines robotics, automation and advanced analytics to provide industrial IoT offerings.
- GE Predix Platform. This IIoT software platform helps connect, optimize and scale digital industrial applications.
- Plataine. Plataine specializes in using AI to generate actionable insights in manufacturing.
- Siemens Insights Hub. Insights Hub offers industrial IoT based on AI and advanced analytics.
IoT and 5G
5G is the standard for mobile networks. It was specifically designed to deliver fast data throughput speeds with low latency. 5G supports download speeds of up to 20 Gigabits per second with sub-millisecond latency.
The emergence of 5G will likely affect the use of IIoT devices in two main ways. First, 5G's high throughput and low latency make it possible for devices to share data in real time. Previously, this was only possible when the devices were located on private networks with high-speed connectivity. This real-time connectivity could support use cases such as driverless cars and smart cities.
The other way 5G will affect IIoT adoption is that it will likely result in device proliferation. Industrial operations could use thousands of 5G-connected devices. 5G's high speed and low latency also means we'll likely see IIoT devices used in remote sites where lack of high-speed connectivity previously made IIoT use impractical.
What is the future of IIoT?
The future of IIoT is tightly coupled with a trend known as Industry 4.0. Industry 4.0 is, essentially, the fourth Industrial Revolution.
Industry 1.0 was the first industrial revolution and occurred in the late 1700s as companies began to use water-powered or steam-powered machines in manufacturing. Industry 2.0 started at the beginning of the 20th century as a result of the introduction of electricity and assembly lines. Industry 3.0 occurred in the latter part of the 20th century and was tied to the use of computers in the manufacturing process.
Today's Industry 4.0 is based on the integration of newer technologies into operations and production facilities. Those newer technologies include cloud computing, artificial intelligence, machine learning and the use of connected electronic devices – particularly, IIoT devices.
Going forward, IIoT devices will play a major role in digital transformations, especially as organizations attempt to digitize their production lines and supply chains. Additionally, big data analytics will evolve to incorporate IIoT data, making it possible for organizations to detect changing conditions in real time and respond accordingly.
Although IIoT devices have been around for several years, real-world adoption is still growing. According to a report from Research and Markets, in 2022, the global IIoT market size was $221.7 billion, and is predicted to grow to $516.6 billion by 2028. Likewise, the development of IIoT as a service stands to become more popular as well.
Adoption rates could also change as 5G becomes increasingly prevalent and more organizations begin to realize what IIoT can do for them. There are numerous online resources available for organizations that want to get up to speed on IoT and IIoT.
Learn more about potential IIoT use cases, as well as more of its advantages and challenges.



